
I’ve just taken and passed the AWS Certified Developer Associate Exam. While I’m basking in the after certification glow I thought I would tidy up and publish my exam notes as a cheat sheet. It’s a pretty long set of notes as there’s a lot to learn. Good luck.
Topics
Acronymns
Common acronymns used throughout the notes
- AZ – availablity zone
- CI/CD – continuous integration / continuous deployment
- CORS – cross-origin resource scripting
- CLI – command line interface
- ETL – extract, transform, load
- IOPS – input/output operations per second
- MFA – multi-factor authentication
- REST – Represention State Transfer – a common API standard
- TTL – time to live
- SSE – server side encryption
- ML – machine learning
Most services also have acronyms (S3, ECS etc..). You should be able to recgonise the service from its acronymn as often the full name isn’t used in the exam.
Tips
It’s a tough exam so some general tips before we start the detail of the various services
1 . Good a study material is key. I recommend Udemy, closely followed by CloudGuru.
2. Know the differences between these sets of services. They often come up
- EBS vs EFS
- Parameter Store vs Secret Manager
- Kinesis Data Streams vs Kinesis Firehose
- SQS vs SNS vs Kinesis Data Stream
- ASG vs ELB
- CloudFormation vs SAM
- CodeDeploy vs CodePipeline
- Cognito User Pool vs Cognito Identity Pool
- AWS API Gateway HTTP API vs AWS API Gateway REST API
3. Know the limits of each service e.g. max item size etc… There is a section called limits for many of the services below to help out.
4. In addition to the study material also use the FAQ section for a service e.g. S3 FAQs. Each services has one and they are a good summary. There are also whitepapers that are recommended for you to read – I didn’t read any and I still passed but perhaps I should have done anyway.
5. Knowing the facts isn’t enough. The questions are scenario based so applying the facts is key. Hands on practice with AWS is best if you aren’t using it in your day to day role.
Keywords
Picking out keywords is useful to give you a clue for instance these keywords point to specific services
- visualisation (think X-Ray)
- audit (CloudTrail)
- compliance (AWS Config)
- metrics (CloudWatch)
- Timeout Errors (Security Groups)
- Continuous Delivery (CodePipeline)
- Timeout Errors (Security Groups)
- Containers (ECS/ECR)
- Real-Time (Kinesis)
and these general concepts will change the correct answer
- serverless
- fully managed
- without changing code
- minimising costs
- minimal effort
Caveats
Everything that follows are my notes from the AWS exam. I’ve tidyied them up a bit but they are still very much in note form. Use them as a basis for your own notes or to cross check for gaps.
General
General resources and required knowledge and cross cutting subjects for the AWS Developer Associate Exam
ARN format
arn:partition:service:region:account-id:resource-id
arn:partition:service:region:account-id:resource-type/resource-id
arn:partition:service:region:account-id:resource-type:resource-idPartitions are the highest level of division.
Supported partitions
aws– Amazon Regionsaws-cn– China Regionsaws-us-gov– Amazon GovCloud (US) Regions
HTTP Response Codes
It’s useful to know the classes of the HTTP reponse codes and the more common specific examples
- 2xx – success
- 3xx – redirection
- 4xx – client error
- 5xx – server error
and specific codes to know
- 200 – success
- 201 – created
- 204 – no content
- 301 – moved permanently
- 302 – moved temporarily
- 400 – bad request
- 403 – forbidden
- 404 – not found
- 408 – request timeout
- 429 – rate exceeded
- 500 – server error
- 502 – bad gateway
- 504 – gateway timeout
Ports
For the exam it is useful to know some ports and port ranges
- 22 – SSH
- 80 – HTTP
- 443 – HTTPS
- 1024-65535 – ephemeral ports. Use for requests from ELB, NAT gateways and Lambda functions
Less likely to come up but possible are the ranges below. Most likely for the AWS Developer exam is just to know that the below operate somewhere in the ephemeral port range.
- 32768 – 61000 – Amazon Linux kernel
- 1025 – 5000 – Windows OS up to Windows Server 2003
- 49152 – 65535 – Windows OS from Windows Server 2008 onwards
Docker
Useful to know basic docker and docker-compose commands e.g.
docker builddocker tagdocker pushdocker rundocker-compose createdocker-compose updocker-compose down
Categories
Remember which services have the below general characteristic.
Global Services
- IAM
- AWS Organisations
- CloudFront
- Route53
- AWS Web Application Firewall
Multi-region services
- DynamoDB – Global Tables
- S3 – cross region replication
- Aurora – Global Database
- VPC – can peer across regions
Encryption by default
- DynamoDB
- CodeCommit
- CloudTrail
- CloudWatch
- X-Ray
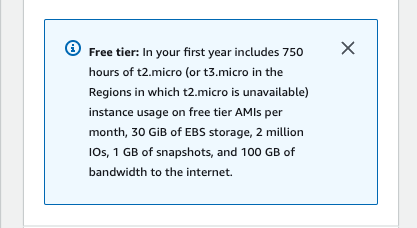
Free Tier
Have a basic awareness of what the free tier offers.
A newly created account as free services within the first 12 months such as
- t2.micro (or t3.micro in certain regions) instances within certain usage limits
from console
Infrastructure as a Service

Services that can be though of as traditional infrastructure that you may find in your own data centres e.g. virtual machines, load balancers, network drives. The nuts and bolts.
Auto Scaling Group (ASG)
Spans multiple AZs across 1 region. Does not span across regions
Will balance EC2 instances across healthy AZs
Health check types
- EC2 and scheduled events (default)
- ELB – works with Application Load Balancers and Network Load Balancers
- Custom
Monitoring options
- Basic – once every 5 minutes. Default when using AWS console to create
- Detailed – once every minute. Default when using SDK or CLI to create
Scaling Policies
https://docs.aws.amazon.com/autoscaling/ec2/userguide/as-scale-based-on-demand.html
- Target tracking scaling – tracks a metric and keeps it at that target value i.e. 50% CPU utilisation
- Step scaling – increases and decreases capacity based on scaling (step) adjustments – scales in proportion to the Cloud Watch alarm beach
- Simple scaling – increases/decreases capacity based on a metric with a cooldown period between each metric
- Scheduled Actions – scaled based on a known usage pattern e.g. 5 pm Friday
- Predictive scaling – continuously forcast based on usage patterns – Machine Learning powered
Metrics to scale on – examples
- CPUUtilizations
- RequestCountPerTarget
- Average Network I/O
CloudFront
Caches web content near to location of user to improve latency
Can have mulitple origins so can source different data from different locations
Used to serve
- Static content e.g. from S3 servers
- Dynamic content e.g. from webservers such as EC2 instances and ECS containers
Origin Groups
Origin groups configure a primary and secondary source. Secondary source used in the event of a failure in the primary therefore providing higher availabilty of the service.
CloudFront only fails over on GET, HEAD or OPTION requests.
Need 2 or more origins for failover. Only one origin is marked as primary.
Security
Keypairs can only be created by root account. Maximum of 2 key pairs. One of the few legimate usages of the root account in normal operations
Key pairs can now be created by key groups with no root account access. New feature as of time of writing.
Signed Url – secure, time limited access to a resource. Associated signed URL with a policy statement. Precedence over signed cookies
Signed Cookies – used for multiple file access
Elastic Block Storage (EBS)
Network drives
File storage – to attach to a EC2 instances. Can be detatched and reattached to another EC2 instance
Locked to AZ
Volume Types
See here for further details
- General Purpose SSD
- gp2
- gp3
- Provisioned IOPS SSD
- io1
- io2
- HDD – cannot be used as boot volumes for EC2
- st1
- sc1 -lowest cost volume
General Purpose SSD
1GB to 16 TB
gp2 – Performance is 3 IOPS per GB., Scales linearly,
gp3 – Performance scales independently of volume size. Baseline 3000 IOPS
Max IOPS for both is 16000
See here for details
Provisioned IOPS SSD volumes
4GB to 16TB.
Max IOPS
- Nitro 64,000
- Other 32,000
Used for I/O intensive workloads – e.g. database workload
Used for I/O intensive workloads
IOPS capacity – max IOPS capacity is 50:1 ratio for storage size to IOPS (IOPS:GB ratio 50:1) e.g. for a 200GB SSD the the max IOPS is 200 * 50 = 10000 IOPS
io2 Block express – 4GB – 64TB, max iops 256,000, IOPS:GB ratio 1000:1
Monitoring
Create volume event – not available when volume created during EC2 launch
Volume status checks – track and manage potential data inconsistencies
Encryption
Encryption by default – regional setting. All new EBS volumes are encrypted. Cannot be disabled on a per volume basis
Cannot directly encrypt and unencrypted volume. To encrypted an existing volume
- create a snapshot
- while copying snapshot enable encryption
- create encrypted volume from encrypted snapshot
Multi-Attach
Only available for io1/io2. Within same AZ. Up to 16 EC2 instance at a time
Other volumes can only be attached to one EC2 instance
Settings
DeleteOnTermination controls if the associated EBS volume will be deleted on instance shutdown. Can be set on console or CLI (and API?) – if using cli then can configure on a running instance. By default set to true for root volume and false for other associated volumes.
DisableApiTermination controls if instance can be terminated by using console, CLI or API
Elastic Cloud Computing (EC2)
Virtual machines. The classic AWS offering.
Cost model
- Spot Instance
- Reserve Instance
- Standard Reserved Instance
- Convertible Reserved Instance
- Scheduled Reserved Instance
- On demand instance
Reserved instances can reserve for cost savings and optionally capacity
- Zonal reserved instance – reserved for cost and capacity
- Regional reserved instance – reserved for cost only
when reserving cost can be appliied across instances – e.g. buying 1 hour can run 2 instances of the correct class for 30 minutes each.
Tenancy
- Dedicated instances – Isolation at hardware level. May share with other instances from same AWS account
- Dedicated hosts – Isolation at hardware level. Control over how instances are placed on server. Used in need to put licence on server. Can deploy to same physical server over time
Metadata
Instance described by http://169.254.169.254/latest/meta-data
User data on launch described by http://169.254.169.254/latest/user-data
Spot Instances
Interrupt behaviour can be
- Stop
- Hibernate
- Terminate – default behaviour
Burstable Instances
Used for variable loads. T family (T4g, T3a, T3). Pricing works on earning credits for time spent below baseline (Burstable Credits). Can be reset by immutable deployment or deployment with traffic splitting.
Monitoring
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/viewing_metrics_with_cloudwatch.html
- Basic monitoring – sends data to CloudWatch every 5 minutes
- Detailed monitoring – sends data to CloudWatch every 1 minute
- High resolution custom CloudWatch alarm with script in EC2 to push data – push data up to maximum of 1 second with an CloudWatch Alarm that evaluates a maximum of once every 10 seconds
Metrics captured by default
- CPU: CPU Utilization, CPU credit usage (count), CPU credit balance (count)
- Disk: Disk reads (bytes), Disk read operations (operations), Disk writes (bytes), Disk write operations (operations)
- Network: Network in (bytes), Network out (bytes), Network packets in (count), Network packets out (count)
- Status check failed (count): any, instance, system
Note – system level RAM usage is not available by default so must be pushed to CloudWatch by a script
Elastic Container Service (ECS)
Container orchestration. AWS equilavent of Kubernetes although elastic kubernetes is also offered.
Service scheduler – can run batch or single tasks.
Step scaling policy – AWS recommends target tracking alarms not step scaling
If multiple containers share a task then they share underlying resources e.g. data volumes
ECS Container Agent
https://docs.aws.amazon.com/AmazonECS/latest/developerguide/ECS_agent.html
ECS container agent allows EC2 instances to be used as hosts. Also be used by external instances (VMs, on-premise)
Config
- in
/etc/ecs/ecs.configfor Linux - Powershell SetEnvironmentVariable for windows
Can pass config via user data into EC2 host
Environmental variables – all optional (examples)
ECS_ENABLE_TASK_IAM_ROLE– IAM roles for tasks with bridge and default network modesECS_ENGINEAUTH_DATAECS_AVAILABLE_LOGGING_DRIVERECS_CLUSTER_NAME– ecs cluster that container should join
ECS structure
- cluster
- container service
- VPC configuration and security groups
- Autoscaling
- container task
- task execution role – i.e. permissions
- memory and cpu
- environmental variables
- port mappings
Fargate Host
Fully managed. Cannot access underlying server.
Considered serverless
Doesn’t support Docker volumes
API
aws ecs create-service --service-name xxx --task-definition xxx --desired-count 10
Elastic Container Repository (ECR)
Amazon hosted repository for containers – like publishing to Docker but in AWS
Elastic File Service (EFS)
File storage
Support for Fargate or EC2
Bind to muliple containers or EC2 instances so used for sharing files
Can only mount on Linux EC2. Windows is not supported.
Mounted on 100s of EC2 instances across AZs
Storage classes
Ordered by decreasing cost
- Standard – High durability, High availability, Frequent access
- Standard-IA – High durability, High availability, Infrequent access
- One Zone – High durability, Lower availability, Frequent access
- One Zone – IA – – High durability, Lower availability, Infrequent access
ElastiCache
Caching layer for your applications
Memcache or Redis
Useful for improving latency and throughput
- read heavy applications
- improving latency and
Need to change code to use this
Caching strategies
- Write through
- Lazy loading
Data partitioning
Memcache and Redis support data partitioning – i.e. distribution of data among multiple nodes. Protects against data loss. Increases read capacity but not write capacity.
All nodes must be in same region. Data is copied from primary node to replicas asynchronously.
Operates independently of cluster mode. If there is a failure with cluster mode is enabled then data loss is partial. If there is a failure with cluster mode disabled then data loss is total.
Memcache vs Redis
https://aws.amazon.com/elasticache/redis-vs-memcached/
Memcache is simpler option
Redis offers advance datastructure storage, snapshots, replication, geospatial capabilities and pub/sub. Memcache doesn’t. Generally Redis is the correct option.
Redis Cluster mode
- horizontal scaling to 100TB. Scale in and out number of shards. Up to 90 shards
- vertical scaling. Changing the node type
- Good for workloads that are unknown in advance
- Includes replication so better protection of data in cache – helps when rengerating the cache is costly
Limitations
- Cannot manual promote read replicas to primary
- Multi-AZ is required
- Need to restore from backup to change structure of cluster (type, number of nodes etc..)
Elastic Load Balancer (ELB)
Load balancing traffic to applications
Targets across multiple Availability Zones in same Region
Cross zone load balancing will distribute traffic evenly against all instances. Enabled on ALB by default
Types of load balancers
- Application Load Balancer
- Network Load Balancer
- Classic Load Balancer
- Gateway Load Balancer
Details of are given below.
Application Load Balancer (ALB)
Works on OSI Layer 7 – Application Layer
Target types
- Instance ID – routed by primary private IP
- IP – routed by any private IP. Cannot specify public IPs
- Lambda
Modified incoming requests. Client details are in these headers
- X-Forwarded-For contains client IP
- X-Forwarded-Proto contains client protocol
- X-Forwarded-Port contains client port
Supports round robin or sticky session routing algorithms
Sticky Sessions require client to have cookies enabled – uses a cookie called AWSALB
Pass through mode vs terminate. Terminate to reduce load on underlying instances.
Logging
ALB request tracing. Adds header X-Amzn-Trace-Id. When load balancer receives then appends information to the header.
ALB access logs- can be used to analyse latency. Optional – not enabled by default. Stored in S3 buckets. Contains information on
- time recieved
- client IP address
- latencies
- request paths
- server responses
Request based routing
Can route requests to target based on
http headers e.g. user agent string
[
{
"Field": "http-header",
"HttpHeaderConfig": {
"HttpHeaderName": "User-Agent",
"Values": ["*Chrome*", "*Safari*"]
}
}
]host header e.g. hostname
[
{
"Field": "host-header",
"HostHeaderConfig": {
"Values": ["*.example.com"]
}
}
]request method (GET, POST etc..)
[
{
"Field": "http-request-method",
"HttpRequestMethodConfig": {
"Values": ["GET"]
}
}
]path i.e. url pattern matching
[
{
"Field": "path-pattern",
"PathPatternConfig": {
"Values": ["/img/*"]
}
}
]query string
[
{
"Field": "query-string",
"QueryStringConfig": {
"Values": [
{
"Key": "version",
"Value": "v1"
},
{
"Value": "*example*"
}
]
}
}
]
source ip
[
{
"Field": "source-ip",
"SourceIpConfig": {
"Values": ["192.0.2.0/24", "198.51.100.10/32"]
}
}
]Troubleshooting
- HTTP 403 – Forbidden, Request blocked by WAF (firewall)
- HTTP 500 Internal server error – ACL in firewall, VPC internet access not working. Request submitted with no protocol
- HTTP 502 Bad Gateway – Lambda throttled or timedout. Target response malfiormed
- HTTP 503 Service unavailable – target groups have no registered targets
- HTTP 504 Gateway timeout – Connection timed out to target, network ACL config
Network Load Balancer (NLB)
Works on OSI Layer 4 – Transport Layer. Very fast and high capacity
Does not modify incoming requests
Target Types
- Instance ID
- IP – cannot specify public IPS
- ALB
ALB vs NLB
https://blog.cloudcraft.co/alb-vs-nlb-which-aws-load-balancer-fits-your-needs/
Classic Load Balancer
Depreciated but still referenced on AWS Developer Associate exam as option. Unlikely to be the answer
Cannot dynamically associate ports
Serverless

Services which do not require you to manage the underlying infrastructure – in fact you can’t.
Services considered serverless are
- DynamoDB
- S3
- ECS (Fargate)
- ECR
- Lamdba
- Step Functions
- SQS
- API Gateway
- App Sync
- S3
- EFS
- Aurora serverless
- Amazon EventBridge
Some are detailed in other sections
AppSync
Managed service that uses GraphQL
- GraphQL api
- real-time with with websockets
- mobile apps for local data access and data sync
Security
- API key
- Iam
- OpenID
- Cognito User Pools
For https – use CloudFront in front of app sync
API Gateway
Mapping templates allow you to change requests and responses to and from the api
Used for creating
- HTTP APIs
- REST APIs
- WebSocket APIs
Supports SOAP by
- configuring as a pass through
- can convert XML response to JSON
Supports Account Level Throttling
Integration Types
https://docs.aws.amazon.com/apigateway/latest/developerguide/api-gateway-api-integration-types.html
- AWS – integration with AWS sevices
- AWS_PROXY – direct integration with Lambds function. Preferred for Lambda
- HTTP – expose http endpoints
- HTTP_PROXY – expose http endpoints with no request or response mappings
- MOCK – used for API testing
Security
Authentication and Authorisation by
- Resource policies
- AWS IAM roles and policies
- Lambda authorisation
- VPC endpoint policies
- Amazon Coginto User Pools
Can restrict access by CORS
Lambda authorisers
Used when
- implement a custom auth scheme e.g. OAuth, SAML.
- Using request parameters to establish use identity
Can be
- Token based
- Request based
Can interface with a 3rd party provider (contrast to Cognito User Pools)
HTTP vs REST APIs
| HTTP | REST | ||
| Security | Mutual TLS authentication | Y | Y |
| Certificates for backend authentication | Y | ||
| AWS Web Application Firewall | Y | ||
| Resource Policies | Y | ||
| Authorisers | Lambda | Y | Y |
| IAM | Y | Y | |
| Amazon Cognito | Y | Y | |
| Open ID Connect /OAuth 2.0 | Y |
Deployments
Canary release to test a deployment with a small amount of traffic
Stabe variables are name value pairs that can be set per environment. Equivalent of environmental variables in Lambda.
Performance
Use API caching
Support API Gateway caching – TTL is 0 to 3600 seconds with a default of 30 seconds
Lambda
Serverless computing in small functions – cheap.
https://docs.aws.amazon.com/lambda/latest/dg/best-practices.html
Test locally with Lambda Runtime Emulator
Temporary files can be stored in \tmp
Not connected to a VPC by default but can be enabled
Permissions
Execution role – gives permission for lambda to access other resources
Resource policy – gives permission for other services to execute lambda
Concurrency
Reserved concurrency – reserves a block of concurreny for exclusive use of function but also limits function to that block so effectively throttles it
Provisioned concurrency – enables scaling without latency. Does not throttle
Logging
console.log statements will log into CloudWatch and can be analysed from there. Don’t use CloudWatch events to log
Deploying
In containers
- Must be in same account
- Max image size 10GB
- Container image must implement Lamdba Runtime API
- Only Linux is supported
To cloudfront – Lambda@Edge provides access to function near to the client geographic location
Dependencies
To deploy dependencies in a Lambda
- Include directly in zip
- Use lamdba layers
- Use custom runtime
Alias
Used to point to a version of a lambda. Aliases cannot point to other aliases
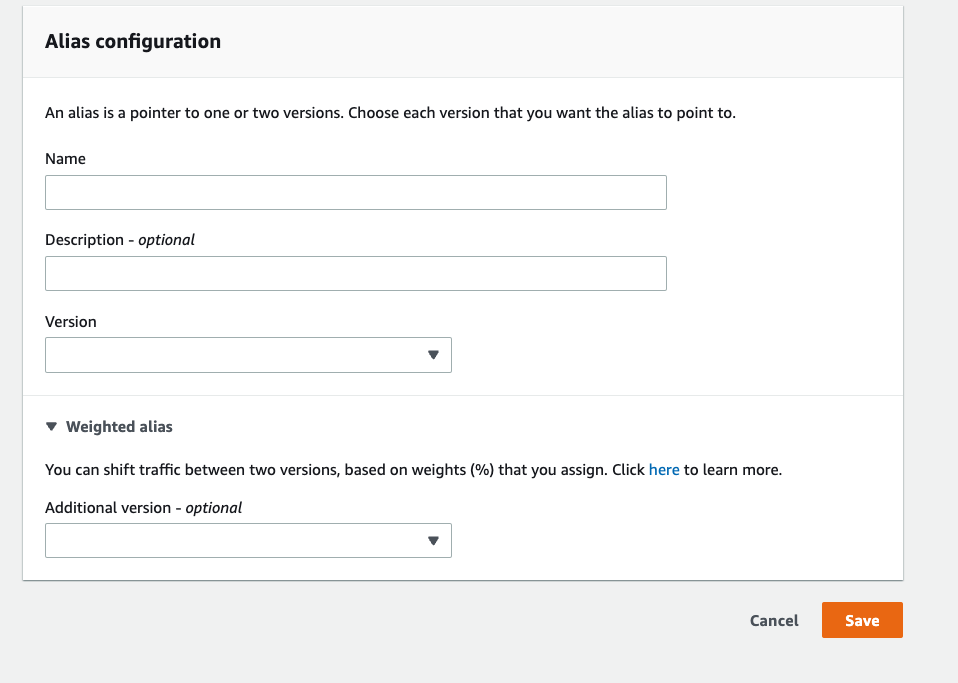
Weighted aliases can be used for a canary deployment
If an unqualified ARN of the lambda will always point to the latest version
Limits
Maximum execution time is 15 minutes
Maximum size of environmental variables – 4KB
Maximum size of lamdba for direct upload – 50 MB. If > 50 MB consider uploading to S3 bucket or using Lambda Layers to reduce size of dependencies
Maximum RAM available foer execution – 10,240 MB
Simple Storage Service (S3)
Serverless file storage
S3 Transfer acceleration for increased performance to and from S3
Security
For ways to control access
- IAM policies
- Bucket policies
- Access Control Lists (ACL)
- Query String – this is for pre-signed url can grant time limited access to resources in otherwise private buckets
ACL vs bucket policies vs IAM policies
Contrast Cloudfront signed url with S3 presigned url
Logging
Amazon S3 Data Events – to log object level activity in CloudTrail – logged as CloudWatchEvents into S3 buckets
Encryption Types
- SSE-S3 – Server side encryption with S3 managed keys. Uses Advance Encryption Standard (AES-256). Key regularly rotates
Resource encryption header –"s3:x-amz-server-side-encryption":"aws:AES256" - SSE-KMS – Server side encryption with KMS managed keys
Resource encryption header –"s3:x-amz-server-side-encryption":"aws:kms" - SSE-C – Server side encryption with Customer managed keys
Resource encryption header –"s3:x-amz-server-side-encryption-aws-kms-key-id" : "key:arn" - Client side encryption
Must use HTTPS for SSE-C.
IAM role needs kms:GenerateDataKey permission if using SSE-KMS – as it’s using envelope encryption it needs permission to create its own key.
Can enable encryption by defaukt to ensure that all new objects are encrypted.
Storage classes
https://aws.amazon.com/s3/storage-classes/
- S3 Standard
- S3 Intelligent-Tiering
- S3 Standard-IA
- S3 One Zone-IA
- Glacier Instant Retrieval
- Glacier Flexible Retrieval — Retrieval time minutes to hours
- Glacier Deep Archive. Retrevial time 12 hours
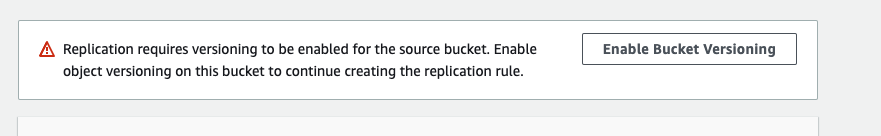
Replication
- SRR – Same-Region Replication
- CRR – Cross Region Replication
Configured at bucket, shared prefix or object level.
Buckets must have versioning enabled (source and target) for replication
Versioning
Items without a version have a version of null. If versioning applied – pre-existing items still have verison of null
Enables recovery of deleted items and restoring of old versions of items
Versioning enabled at the bucket level
Consistency
S3 buckets are strongly consistent for GET, PUT, LIST, DELETE operations and metadata and ACL operations for objects within a bucket
S3 bucket configuration are eventually consistent for information about the buckets themselves e.g. list all buckets in an account
Events
Examples
S3:ObjectCreateS3:ObjectRemoveS3:ObjectRestoreS3:Replication
Event targets are
- SNS
- SQS
- Lambda
- Event Bridge
Events are designed to be fired at least once – therefor possible to have muliple events for same action. If bucket is versioned then will get one event only per CRUD event
CLI
s3 list-object lists all S3 objects
page-size– smaller number of items returnedmax-items– maximum number of items returnedstarting-token– used for paging results. Gets a starting point for that page
Limits
5GB limit for single PUT operation
If >100MB the recommended us multi-part upload
Maximum size for multi-part upload is 5TB
Range for S3 object sizes are 0 bytes to 5YB. Total storage in S3 is unlimited.
Step Functions
Manages tasks in a stateful workflow. Defined as JSON
Made up of
- tasks.
- state machines – make the decisions
- activity worker – polls for a task
Serverless – contrast to SWF
Allows task retries
Cannot be used to run Docker containers
States
- Task
- Choice
- Wait
- Pass
- Fail
- Timeout
- Succeed
- Map – dynamically iterate through steps
- Parallel State
State Machines
Actions can be
- invoke Lambda
- run AWS Batch job
- run ECS task
- Insert item to DynamoDB
- Publish message to SNS, SQL
- Launch anotther step fuction
- Run activity – EC2, On premise, ECS. Polls for work (similar to SWF)
Error Handling
Error handing should be in state machine not in application code
- Retry
- ErrorEquals
- IntervalSeconds
- BackoffRate – for expontential backoffs
- MaxAttempts
- Catch
- ErrorEquals
- Next – direct to another state
- ResultsPath – allows you to include error in output
Standard vs Express
Standard – duration 1 year. Exactly once execution
Express – duration 5 minutes. At least once workflow. Cheaper than standard.
Data

AWS offers many services that manage data and function as structured datastores.
Athena
Used to query data in S3 buckets
Execute SQL on large datasets spanning separate files. Contrast to S3 Select
DynamoDB
Serverless NoSQL database. Multi-region. Fully Managed
Data Type
- Scalar
- Number
- String
- binary
- Boolean
- null
- Document
- List
- Map
- Sets
Primary Key
Made up of
- Partition Key
- Sort Key. Optional.
Supported data type – number, string, binary
Provisioning
The exam will almost certainly ask you to calculate read and / or write capacity for DynamoDB.
Read Capacity Unit (RCU) equals one strong consistent 4KB or less reads per second
Read Capacity Unit (RCU) equals two eventually consistent 4KB or less reads per second
Write Capacity Unit (WCU) equals one 1KB or less writes per second
Scaling
DynamoDB Accelerator (DAX) to improve read speed with no code changes. 10x performance improvements
Global tables replicate tables across predefined regions to reduce latency
Transactions
Supports transactional read and writes for ACID transactions
TransactWriteItems – up to 25 items. The total size must be <= 4MB
TransactGetItems
To ensure that application always has the correct data then use the Consistent Read flag. GetItem Query and Scan can use strongly consistent reads
Conditional Writes – used when mulitple people are updating the record at the same time
Operations
GetItem – read
UpdateItem – edit attributes of existing item
PutItem – adds new item or replaces old item with a new one entirely
BatchGetItem – reads one or more items from one or more tables
BatchWriteItem – writes one or more items to one or more tables
Scan – reads data sequentially in 1MB increments. Inefficient but does not require indexes
Parallel Scans – as above but multi-threaded scanning separate partitions
ProjectionExpression – limited set of attrbutes to return – like the SELECT clause in SQL
FilterExpression – results to be discarded after scan has run. Does not limit RCU
Query – reads only data specified in query. Does limit RCU. Requires an index to cover queried attributes or a partiton key
TTL – define when items from database expire so that can be automatically deleted. Can set on a per record basis
Indexes
Global secondary index – can be created on existing or new table. Can contribute to throttling of the database
Local secondary index – can only be created on a new table
DynamoDB Streams
Ordered flow of information containing changes to a table. Stored for up to 24 hours. Can be cionsumed by other services such as Lambda.
Backup
- Point in time
- On demand
Do not have access to those S3 buckets so can’t use as exports
Permissions
See here for complete list
UpdateItem permission is enough to upsert an item
Limits
Max item size – 400KB
Max GSI – 20 per table. Raise AWS support request to raise
Max LSI – 5 per table
Relational Database Service (RDS)
Relational databases in the cloud.
Types
- Oracle
- MySQL
- PostGreSQL
- MariaDB
- SQL Server
IAM database authentication works with MariaDB, MySQL and PostGreSQL
Auto-scaling
can be enabled so volume increases when
- storage is >90% full for > 5 minutes
- > 6 hours since last storage modification
- Storage is below user defined maximum storage limit
High Availability
Read replicas – used for heavy readonly usage scenarios.
Cross Region Read Replicates also used for HA. In the event of a failure a read replica can be promoted to a full instance.
Multi-AZ – for high availability
- Updates to primary are copied over to secondaries synchronously
- OS updates are performed on secondary which promotes to primary so no downtime
- Backups are taken from standby so no I/O suspension
- Secondaries do not serve read requests so can’t function for performance. HA only
Backups
Manual backups supported across mulitple regions
Automated backups supported on one region only
Deletion protection can be enabled – can’t be deleted by any user or tear down of environments such as with Elastic Beanstalk
Limits
Backup retention period 0 to 35 days
Relational Database Service – Aurora
Highly available cloud optimised RDS.
MySQL and Postgres compatible
High Availability
- Stores 6 copies of data over 3 AZ.
- 3 copies requiered for reads
- 4 copies requied for write
- self healing and striped over 100s of volumes
- One instance is master. Failover in 30 seconds (fast)
- 15 read replicas (mysql has 5)
- cross region replication for read replicas
- Load balancing through read endpoint (contrast to write endpoint)
Storage
Automatically grows up to 128 TB in 10GB increments
Aurora Specfic Functionality
- Database cloning
- Point in time restoration
S3 Select
Use SQL for simple queries on one S3 file. Contrast to Athena
Networking

The developer exam doesn’t often ask questions about networking but understanding networking is often the key to getting the answer right for questions on the other services.
Route 53
DNS Service
Record Types
A Record
Points IPv4 to domain name
CNAME record
Points one domain to another
Cannot create alias for apex domain e.g. can’t use example.com with CNAME but could use subdomains such as www.example.com or subdomain.example.com
Alias Record
Points domain to AWS resource such as S3, CloudFront or another record in that Route 53 hosted zone
Can be an apex zone
Specific to AWS
PTR
Reverse DNS record. Opposite of A record
Routing policies
- Simple routing
- Failover routing
- Geolocation routing
- Geoproximity routing
- Latency routing
- Mulitvalue answer routing – up to eight healthy records selected at random
Virtual Private Cloud (VPC)
AWS Networking – the glue that holds it all together
Route table
set of rules that determine where traffic from subnet/gateway is directed
Internet access
Internet Gateway – internet access for VPC. If a VPC has an Internet Gateway then it becomes public
NAT Instance – internet access to private subnet. The private subnet can contact the Internet but the Internet cannot see the VPC hence it remains private. Contrast to Internet Gateway. NAT Instance is not the name of an AWS Service, rather it is a general networking concept.
NAT Gateway – Service offered by AWS with better performance and easier management as compared to NAT Instance. Preferred if given a choice
Endpoints
Allow communication between instances and VPC – can privately connect VPM to AWS services. No public IP required.
Types
- interface endpoints. Elastic network interface with private IP address
- gateway endpoints. Specify target in route table to traffic destined to service. DynamoDB and S3 have gateway endpoints. S3 also has interface endpoints
Elastic IP – gives an endpoint a fixed public IP address.
NACL vs Security Groups
NACLs and Security Groups both limit traffic based on source IP and port and function as virtual firewalls
| Security Groups | NACLS |
|---|---|
| Associated with EC2, ELB | Associated with subnets(?) |
| Stateful – allowing inbound traffic allows outbound | Stateless – must explicitly allow inbound and outbound traffiic |
Messaging

Messaging systems to decouple and scale yopur applications. Know the differences between them.
Kinesis Data Analytics
Analyses streaming data in real time.
Serverless
Automatically scales
Kinesis Data Streams (KDS)
ingest data in real time
Supports ordering and replay
Multiple consumers
Encryption
Data encypted at rest by KMS customer master key
Data encypted in flight by HTTPS endpoints
Shards
Capacity is defined by number of shards in the data stream – these do not automatically scale
Can have one processing unit (e.g. EC2) per shard
Performance
Enhanced fan out – each consumer gets their own 2MB/sec pipe per shard – contrast to standard where 2MB/sec per shard is shared between all applications.
If capacity exceeded then get ProvisionedThroughputExceeded exception
Supporting software
Kinesis Client Library (KCL) can deliver all records of a partition key to a given client making it easy to support multiple consumers
Kinesis Producer Library (KPL) to write to data stream from application code
Kinesis Agent can be installed on EC2 to capture data to KInesis Data Stream
Limits
Retention period is 7 days
2MB/sec per shard is shared between all of the applications
Kinesis Firehose
Egest data – loads into data stores targets. Contrast to KDS
Automatically scales
Fully managed
More cost effective than KDS
Supported targets
- S3
- Amazon Redshift
- Amazon Elasticsearch
- Generic HTTP endpoints
- Specific 3rd party e.g. Splunk, Datadog, MongoDB, New Relic
Functions
- Load
- Batch
- Compress
- Transform
- Encrypt
Simple Queue Service (SQS)
Supports only 1 consumer – contrast to Kinesis Data Streams
Used with asynchronous clients e.g. Lambda
Queue Types
- Standard message queues – order not guaranteed and possible for message to be read more than once
- FIFO message queues – guaranteed order with each message being read once.
Cannot convert standard queue into a FIFO queue
Performance
In almost all cases use long polling. Decreases number of empty reponses and ensure a message is pulled off as soon as it arrives. Use maximum of 20 seconds for timeout.
SQS Extended Client Library for Java
Used to manage large messages – see Limits
- specify whether messages are always stored in S3 or just when > 256 KB
- sends a message that references content in S3 bucket
- get message from S3 bucket
- delete message from S3 bucket
Limits
Minimum message size is 1 byte
Maximum message size is 256KB
If a message is > 256 KB then use SQS Extended Client Library for Java. This supports messages up to 2GB. If > 2GB then store messages in S3 and reference from a pointer in the SQS message.
No limit on the number of messages stored
Maximum of 10 messages can be recieved at one time by a consuming application
Message rention
- default 4 days
- minimum 60 seconds
- maximum 14 days
Standard – Approx 120,000 limit of number of inflight messages
FIFO – 20,000 inflight messages
Autoscales on demand within the above limits
Configuration
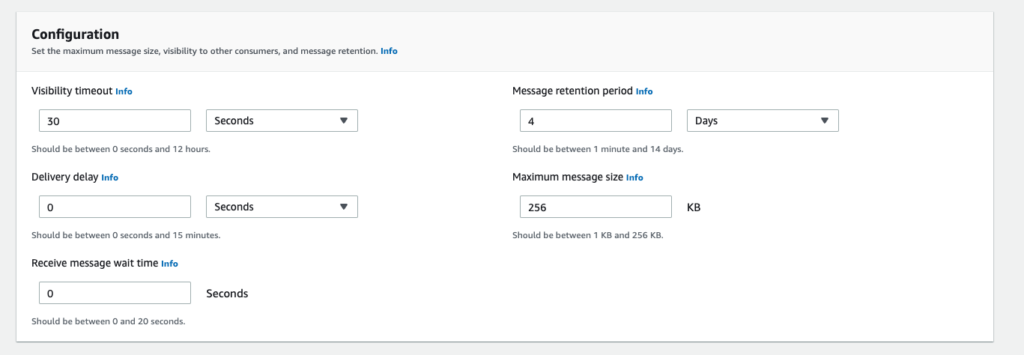
WaitTimeSeconds to set short polling vs long polling. Minimum 0 seconds, maximum 20 seconds
MessageRetentionPeriod
DelaySeconds – min 0 seconds, max 15 minutes
ChangeMessageVisibility helps prevent mulitple consumers processing the message
- Default value – 30 seconds
- Minimum value – 0 seconds
- Maximum value – 12 hours
FIFO configuration
MessageGroupId – the messages are ordered within this grouping. Ordering is not guaranteed between groups.
MessageDeduplicationId – messages with the same deduplication id aren’t redelivered within a 5 minues interval. Guarantees exactly once processing.
ContentBasedDeduplication – use SHA-256 hash to base deduplication on body of message rather than the MessageDeduplicationId
API
- PurgeQueue
- DeleteQueue
- RemovePermissions
Security
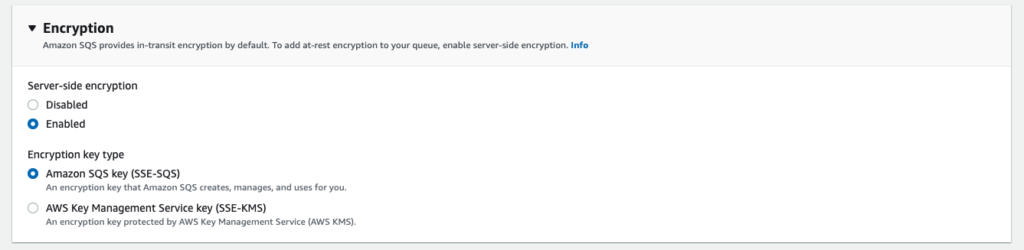
For encrypted queues enable SQS KMS encryption
Simple Notification Service (SNS)
Pub / sub messaging system supporting multiple subscribers
Integrates with ..
- SQS – for Fanout pattern
- Lambda
- Kinesis Firehose
- etc…
Can send messages in types of
- Notifications to other AWS services
- Emails
- SMS messages
- Mobile push notifications
Simple Workflow Service (SWF)
Manages tasks in a stateful workflow. Users decider programs
Task assigned only once – contrast to SQS where can deliver message multiple times
Need to manage infrastructure – contrast to step functions
Logging and Monitoring

Logging comes up over and over again in the AWS developer exam. Know this in detail, especially CloudWatch.
Amazon Event Bridge
Event-driven applications
Only event based system that integrates directly with third party SaaS systems
Supported sources
https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-service-event.html
- Athena
- CloudFormation
- CloudTrail
- CodeBuild
- CodeCommit
- CodeDeploy
- Elastic Beanstalk
- EBS
- EC2
- ECR
- ECS
- KMS
- RDS
- S3
- Step Functions
- Plus others not on AWS Developer Associate Exam
Scheduled Tasks
https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-create-rule-schedule.html
Can create a rule that runs on schedule i.e. running a Lamdba function every hour
Types
- cron expressions. Cron expressions of a rate faster than 1 minute are not supported
- rate expression to run on a defined schedule e.g. every 5 hours
Examples
- Event from EC2, target SNS. Email when things happen on EC2 instance
- Event from CodeBuild, target SNS. Notifications when build completes
- Event from CodeDeploy, target lambda. Run custom code at particular stages of a deployment
AWS Config
resource history, audit and compliance
CloudTrail
Account specific activity and audit e.g.
- actions through management console
- actions through SDK
- actions through CLI
- API calls E.G. to KMS, SSM, Lambda, API Gateway – see here for a full list
- Failed logins
By default only logs S3 bucket level events not object level
Encrypted by default – SSE
Trails
Can create trails for
- All regions
- One region
- Organisation trail for all regions
- Organisation trail for one region
Integrations
- CloudWatch logs – can direct to another service or stream into an S3 buckets
- CloudWatch events – can take actions depending on cloudtrail events
Limits
Stores 90 days of activity within AWS account
CloudWatch
Performance monitoring, events and alerts
Integrates with S3
Can view events from mulitple applications on a single dashboard – across region if required.
CloudWatch Agent
- Collects logs and / or metrics from EC2 instances
- Collects logs and / or metrics from on premises services and forwards to CloudWatch
- Works with Linux or windows
Custom monitoring
Use PutMetricData to push data from EC2 into CloudWatch. Can be standard resolution or high resolution (push every second)
GetMetricStatistics – for high resolution metrics can be 1,5,10,30 or 60 second intervals. For standard resolution can be any multiple of 60 seconds.
Metric retention
The data points storage is dependent on metric resolution
| Resolution | Data Frequency | Retention Period |
| High | < 60 seconds | 3 hours |
| Standard | 60 seconds | 15 days |
| Standard | 5 minutes | 63 days |
| Standard | 1 hour | 15 months |
CloudWatch Alarms
Performs an action when data is over a threshold e.g.
- SNS topic push
- ASG policy
Possible states for alarm
- OK
- ALARM
- INSUFFICIENT_DATA
PutMetricAlarm – creates a cloud watch alarm
Cloud Watch Events
Superceded by Event Bridge
Security
Cloud watch logs are always encrypted
Use API call associate-kms-key to encrypt CloudWatch logs with a KMS key as an alternative encryption method
Use API call describe-log-groups to see if a log group is already associated with a KMS key
X-Ray
Logging and visualisation. Useful for microservice architecture
Sends data as segments
Each participating instance (EC2 or ECS) needs access to X-Ray Agent. EC2 can have agent installed but ECS needs an additional sidecar container to host the agent.
Encrypted at rest by default. Can specify a KMS customer managed key.
Integrations
X-Ray can integrate with
- Lambda
- API Gateway
- Elastic Load Balancer
- Elastic Beanstalk
- SNS
- SQS
- S3
Configuration
- Sampling – by default it samples first request each second then 5% of total requests. Decrease sampling rate to minimise costs if required
- Annotations – key-value pairs used to filter and group traces in console. Are indexed
- Metadata – key-value pairs. Additional information that are not required for search
Environmental variables
- AWS_XRAY_DAEMON_ADDRESS – host and port of X-Ray (Daemon – agent?) if not default (127.0.0.1:2000)
- AWS_XRAY_TRACING_NAME – service that SDK uses for segments
Deployment

Deployment of applications and provisioning of AWS infrastructure.
AWS Amplify
Create mobile and web apps. Like elastic beanstalk but for web and mobile apps
amplify add auth – Authentication using Cognito
amplify add api – uses GraphQL and DynamoDB
ampify add hosting = CICD, domains etc…. Like vercel
CodeArtifact
Code artifact management – integrates with npm, yarn, Maven, nuget, pip etc…
Repositories in domain – so use npm targetted at CodeArtifact. Is a proxy into npm. Good for
- network security
- cached – in case public repository disappears
Also can push own artifacts
CodeBuild
Managed build system.
Build specific environmental variables. Don’t need to know full list for AWS Developer Associate Exam
buildspec.yml in application root contains build config
Fully managed – scales automatically to meet peak demand
Limits
The maximum number of builds in the queue is five times the number of concurrent builds that can be run.
Security
Can encrypt build output artifacts by specifing a KMS customer managed key. Use environment variable CODEBUILD_KMS_KEY_ID
CodeCommit
Repository based on Git
Encrypted at rest and inflight by default
Authentication and access
https://docs.aws.amazon.com/codecommit/latest/userguide/auth-and-access-control.html
Cannot use IAM username and password to access directly
Can generate SSH keys or Git Credentials from IAM
Notifications
Can be created in the console
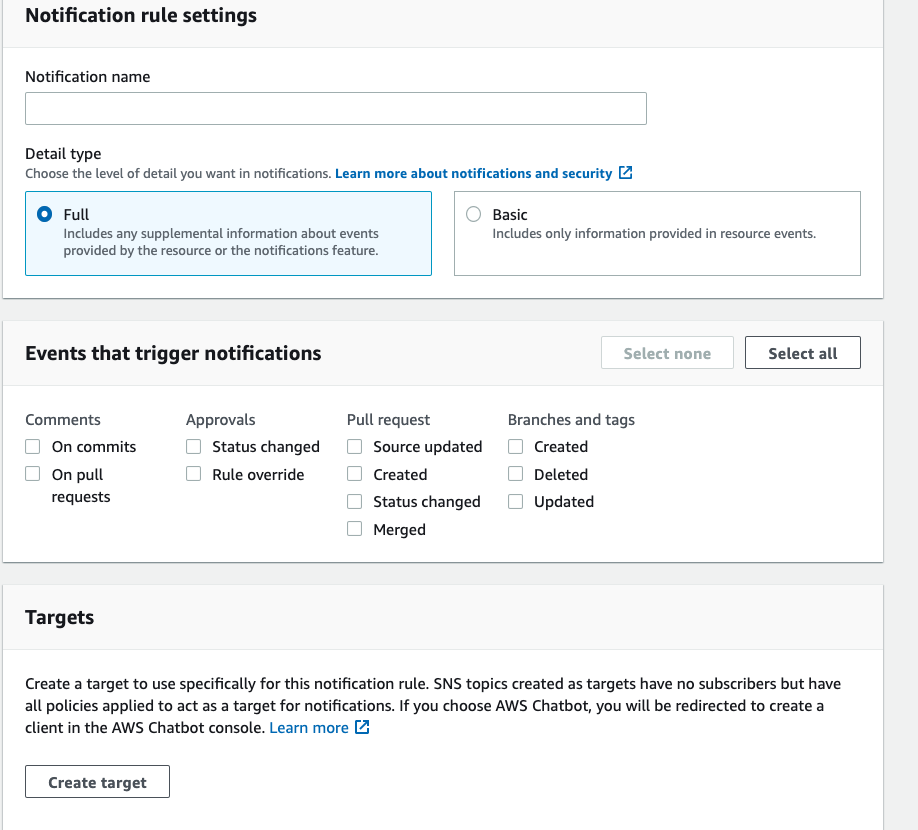
will create an event rule which can be used to publish to SNS
CodeDeploy
Fully managed application deployment. Automatically scales
Types
- In-place
- Blue/Green
Supported Platforms
- EC2
- Fargate
- Lamdba
- On premise server
appspec.yml in the root directory of the application defines deployment config including
- map source files to destination
- custom permissions for deployed files
- scripts to run at each stage of deployment
- deployment preconditions i.e. what must be installed on deployed instances
appspec.yml for EC2/on premise deployment and Lambda
appspec.json for Lambda. EC2 and on premise not supported in this format
Deployment hooks
Used to run code or trigger events. In order ….
- ApplicationStop
- DownloadBundle
- BeforeInstall
- Install
- AfterInstall
- ApplicationStart
- ValidateService – last deployment event. All below can’t be used to run deployment scripts
- BeforeBlockTraffic
- BlockTraffic
- AfterBlockTraffic
- BeforeAllowTraffic
- AllowTraffic
CodeDeploy Agent
Installed on instances to be deployed.
- archives application revisions
- archives log files
- cleans up disk space –
:max_revisionoption in config
Can be installed on local machines to debug failing builds. Need buildspec file locally
Deployment Groups
Contains settings and config used for a deployment.
In EC2 or on premise deployments this can be a set of instances to deploy to
CodePipeline
Fully managed CI / CD solution.
- source – CodeCommit, GitHub etc…
- build – Jenkins, CodeDeploy
- test
- deploy – CodeDeploy, EB
Contrast to CodeDeploy – if question mentions CI / CD then favour this service
Output of stages are stored in S3 and are picked up by downstream services from S3 e.g. build output, project artifacts etc..
Use Cloud Watch Events to react to changes in the pipeline
Supported code sources
- CodeCommit
- S3
- GitHub
CodeStar
Unifies CI/DC in one dashboard. Simplified management. Don’t get all config options.
Integrated issue tracking with Jira
Cloud Development Kit (CDK)
Programmatic variant of CloudFormation
Steps
- Initialise templates
cdk init - Write the code
- Build (optional)
- Synthesize the stacks (optional but good practice)
- Deploy by
cdk deploy
CloudFormation
Infrastructure as code. Declarative in JSON or YAML format.
Cannot be used for
- Certificate Management
- Server patching
Template Anatomy
Template anatomy details
- Parameters – cannot have a condition
- Conditions – defines conditions to be used elsewhere
- Resources (only mandatory section)
- Outputs – contains export field used for cross stack referencing
- Export – unique name within region
Parameters
Supports the following parameters
- String
- Number
- List<Number>
- CommaDelimitedList
- AWS::EC2::Keypair::KeyName – EC2 key pair name
- AWS::EC2::SecurityGroup::Id – Security Group Id
- AWS::EC2::Subnet::Id – Subnet id
- AWS::EC2::VPC::Id – A VPC Id
- List<AWS::EC2::SecurityGroup::Id> – Array of Security Group Ids
- List<AWS::EC2::Subnet::Id> – Array of Subnet ids
- List<AWS::EC2::VPC::Id> – Arrhay of VPC Ids
Intrinsic Functions
Pseudo Parameters
- !GetAtt – used to retrieve values from earlier parts of template
- !Ref
- !ImportValue – imports an exported value from another stack
- !Join – joins strings
- !Sub – replaces in string
- !FindInMap – looks up value in predefined mapping table
Pseudo Parameters
- AWS::AccountId
- AWS::Region
- AWS::StackName
- AWS::NoValue – removes resource when used in condition
AWS::CloudFormation::Stack– refers to a nested stack
Deployment
cloudformation package packages and uploads local artifacts e.g Lamdba code
cloudformation deploy executes changeset e.g. creates / updates AWS resources
Lamba code can be deployed in the AWS::Lambda::Function block by
- Inline in the template if there are no third party dependencies
- Zipped into S3 then the zip referenced in the template. This can have dependencies
Changesets used to identify changes for an update in the template
Enable Termination Protection to stop stack being deleted. Can still update the stack and remove resources in that way.
Deletion Policy is used to retain objects when template is changed or removed. Contrast to Amazom RDS DeletionProtection
{
"AWSTemplateFormatVersion" : "2010-09-09",
"Resources" : {
"myS3Bucket" : {
"Type" : "AWS::S3::Bucket",
"DeletionPolicy" : "Retain"
}
}
}Elastic Beanstalk
Simplified deployment of apps. Although it’s simplified there are heaps of options and it’s actually quite time consuming to learn.
Config
Saved configurations are stored in S3 buckets
Config is stored in app code under .ebextensions/mysettings.config
Config file sections
- option_settings
- resources
- packages
- sources
- files
- users
- groups
- commands
- container_commands
- services
Deployment Strategies
- All at once
- Rolling
- Rolling with additional batch
- Immutable
- Traffic Splitting
- Blue/Green
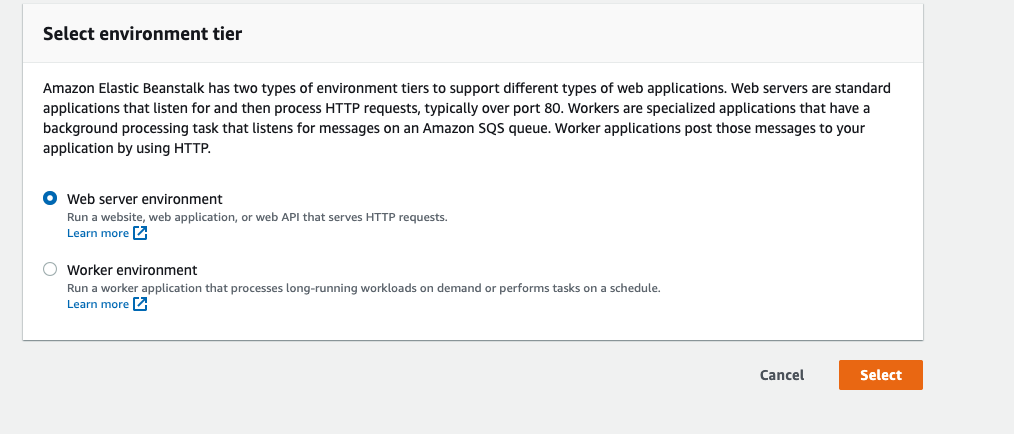
Worker Environments
https://docs.aws.amazon.com/elasticbeanstalk/latest/dg/using-features-managing-env-tiers.html
Used for long running tasks e.g. video processing
Use cron.yml file to define cron jobs for repetitive tasks
Platforms
https://docs.aws.amazon.com/elasticbeanstalk/latest/platforms/platforms-supported.html
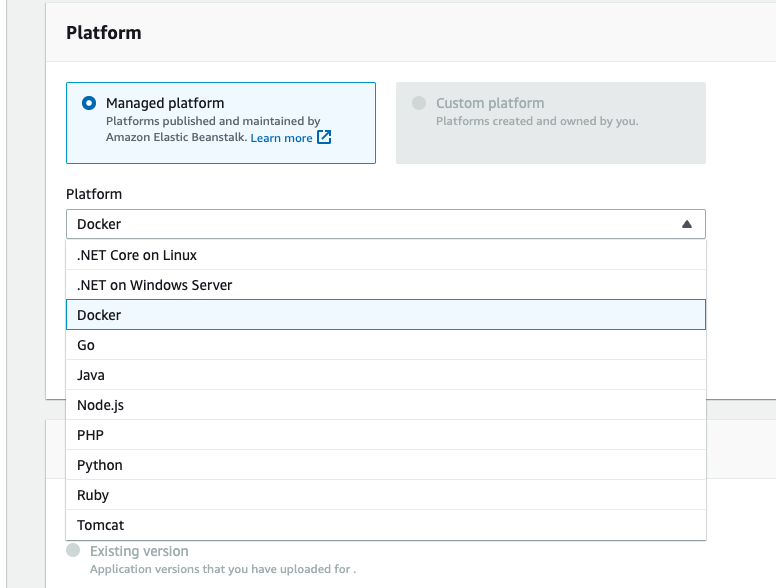
- ‘Popular’ languages and frameworks (Python, Node, Go, .Net etc..)
- Docker single container
- Docker multi container
- Custom – when EB doesn’t support a required language or framework e.g. C++
Linux 1 environments were replaced by Linux 2 environments in July 2022. AWS now recommends Buildfile, Procxfile and platform hooks to customise environments rather than ebextensions – though this is still supported. See https://docs.aws.amazon.com/elasticbeanstalk/latest/dg/using-features.migration-al.html
Custom Platform
- Build AMI from one of supported platforms (all Linux variants)
- add customisations as desired
- Create elastic beanstalk platform using Packer
- root of application must include
platform.yaml
Lifecycle policy
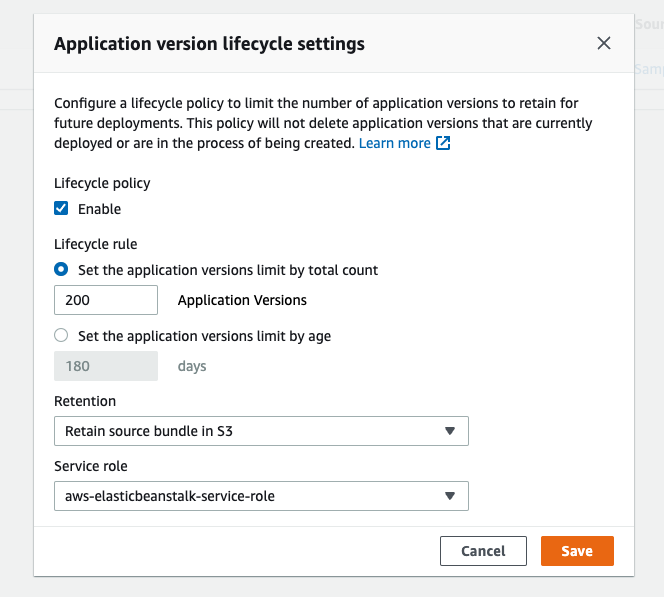
Set a lifecycle policy to remove old versions. Current version doesn’t count towards the total.
Limits
Source bundle for application upload must be < 512MB and be a ZIP or WAR
Serverless Application Model (SAM)
Templates to define serverless infrastructure as code. A simplified variant of CloudFormation
Resource Types
- AWS::Serverless::Api – API Gateway
- AWS::Serverless::Application
- AWS::Serverless::Function – Lambda Function
- AWS::Serverless::HttpApi
- AWS::Serverless::LayerVersion
- AWS::Serverless::SimpleTable – DynamoDB Table
- AWS::Serverless::StateMachine
To use
- Develop template locally
sam deploycommand. This zips application artifacts, uploads to S3 then deploys application to AWS
Security

Managing access and security to your infrastructure. A central concern in the exam. Know it in detail.
AWS Certificate Manager (ACM)
SSL/TLS server certificate management
Can automatically renew
AWS Security Token Service (STS)
Use to request temporary credentials. Created by GetSessionToken call
Gives temporary access to AWS service via access key, ID, secret access key and security token) AssumeRoleWithWebIdentity
get-federated-token – retrieve token for federation
Also decode auth error messages decode authorisation messages
Global service
Limits
Expiry on assumed credentials
- Minimum 15 minutes
- Maximum 1 hour
- Default 1 hour
Cognito Identity Pools
Grant users temporary access to other AWS resources
Supports guest access
Cognito Sync
Cross device syncing of user data for mobile or web
Cognito User Pools
AWS authentication – can use a third party federated provider but the users themselves are managed by AWS
Can be used to track and remember devices. Can use this to limit number of devices that a user can stream content from e.g. Netflix.
Can add MFA to a user pool
Identity and Access Management (IAM)
https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies.html
User and permission management. Global service
Can be used for limited certificate management – only use when region doesn’t support ACM
Might route traffic preferentially to higher capacity instances
Identities
Users, Groups and Roles
Identity Policy
Attached to user, group or role
AWS Managed, Customer Managed or Inline
Examples of policies
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "FullAccess",
"Effect": "Allow",
"Action": ["s3:*"],
"Resource": ["*"]
},
{
"Sid": "DenyCustomerBucket",
"Action": ["s3:*"],
"Effect": "Deny",
"Resource": ["arn:aws:s3:::customer", "arn:aws:s3:::customer/*" ]
}
]
}
Further examples here
Resource Policy
Full list of services that work with IAM
For AWS Developer Associate exam know
- EC2
- ASG
- Elastic Beanstalk
- ELB
- Lambda
Trust Policy
Which IAM entities can assume this role. Only type of resource based policy in IAM
Permission Boundaries
Sets maximum permissions for an entity (user or role)
AWS Organisations Service Control Policy (SCP)
Defines maximum permissions for entities in an Organisational Unit within an Account
Cross Account Access
Use sts:AssumeRole – example Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::AccountB_ID:role/ROLENAME"
}
]
}
Cross account access does not work across partitions
Example
User on account A wants to access Database on Account B
- IAM role in account B with access to database
- Amend trust policy on above IAM role to allow accoutn A to assume it
- Update policy on account A user to allow it to assume role from account B
Tools
IAM Policy Simulator
Tests acess on a per account basis
IAM Access Analyzer
- Identifies resources that are shared outside a given boundary (i.e. an organisation or an account)
- Validate policies – grammar and best practices
- Generates policies from a CloudTrail
Access Advisor – On IAM console. Identifies unused roles over a given time period
--dry-run flag on CLI can be used to test if have required permissions for the action
Certificate Manager
IAM can be used as a certificate manager. Use only when ACM is not available in a region. Certificates must be obtained from an external provider.
Key Management Service (KMS)
Encryption key management
Supports automatic key rotation
Amazon Managed and Customer Managed Keys
Configuration
Key can be locked to one region. Single region by default
Key policies control which account / service can use the key and for what
Envelope Encryption
Use for encrypting target data. The data key itself is encrypted with generate-data-key which returns a plaintext data key and an encrypted key. The plaintext key is used to encrypt the data outside of KMS and the discarded. The encrypted datakey is then stored along with the encrypted data within KMS.
Envelope encryption is used to
- Encrypt items > 4KB
- Encrypt a data encryption key for greater security
CLI
encrypt
decrypt
re-encrypt – used to swap encryption keys
enable-key-rotation – configures key rotation
Limits
Maximum data size is 4KB. For anything over this Envelope encryption is used.
Secret Manager
Stores sensitive data such as user names and passwords
Can automatically rotate secrets
Integrates with RDS, Amazon Redshift and Amazon DocumentDB so can change credentials of those services automatically
SSM Parameter Store
AWS Systems Manager Parameter Store
Can be secrets and stored as SecureString but no automatic rotations. Contrast with Secret Manager
Other Services
These services come up in the AWS developer exam but often as distractors. They are less likely to be the correct answer. Knowlege of the details are not needed
- Amazon Inspector – automated security assessment
- Amazon Redshift – data warehousing
- Amazon EMR – big data
- AWS Batch – runs batch jobs and provisions resources
- AWS Data Pipeline – moving data between sources and targets
- AWS Global Accelerator – network service to improve traffice performance
- AWS Glue – extract,transform, load
- AWS Trusted Advisor – guidance on security, fault tolerance, cost optimisation
- AWS Web Application Firewall (WAF) – Firewall – can deploy on CloudFront or Application Load Balancer.
- CodeGuru – ML powered service for code reviews and preformance recommendations
- Serverless Application Repository (SARS) – Marketplace for serverless apps
- Systems Manager (SSM) – used to group and manage resources
- Simple Email Service (SES) – email sending
And if you have to guess…
Here are a few tips and broad rule of thumbs for the exam. When you are forced to take educated guesses then these might improve your odds of guessing right.
Rules of thumb
- Root account shouldn’t be used routinely – it’s almost always the wrong answer to use the root account for anything – exceptions CloudFront access keys and these have now been superceded by key groups anyway
- Anything that looks like an error condition is probably the wrong answer e.g. command line use results in erratic behavour
- Similarly, if an answer is that an AWS service is down or unavailable for some reason that is almost certainly the wrong answer. AWS never goes down.
- Most things (but by no means all) work within a region so guess the option that doesn’t cross regions if you have to. Not a great guess but you are playing the odds here.
- It’s very rarely the right answer to contact AWS helpdesk. An exception could be if you wanted the soft limit on a service raised
- Exponential backoff is preferred for throttling issues across a number of services
- Generally if something seems insecure it’s probably wrong e.g. unecrypted disks and inflight http messages
- It’s not a bad guess to say that something used by a service is uploaded to S3 as an intermediate stage (rather than uploaded elsewhere such as EBS, CodeCommit, EC2 etc…). Services that do this include CodePipeline, CloudFormation, SAM etc….
Bad practice
If you can identify something as dodgy practice then you can rule it out as an answer. Examples …
- Sharing credentials
- Making S3 buckets public without a good reason
- Routing VPC traffic over the Internet without a good reason
- passwords in code or clear text
- giving unnecessary permissions – principle of least privilege
Legacy options
Certain options are legacy or are generally not a favoured option by the AWS Developer Exam so don’t pick these unless you are certain. Examples …
- Classic Load Balancer. Prefer ALB or NLB
- SWF. Prefer Step Functions for stateful workflow management
- ASG Step scaling. Prefer target tracking scaling policies
- CognitoSync. Prefer AppSync
And as I said at the beginning, good luck!
Additional Useful Links
Additional information useful for AWS Developer Exam
Well Architected Framework
https://aws.amazon.com/architecture/well-architected
Global vs Regional resources
https://jayendrapatil.com/aws-global-vs-regional-vs-az-resources/





Thank you for posting this, it is very helpful to have all this information posted in one place. I’ll be taking my DVA-C02 shortly.
It helped me revise all the concepts before the exam. Planning to attempt DVA-C02 by the end of this month.
This is awesome, thanks for posting, will be taking my exams in June.